Breadcrumb
Innovative approaches to metabolic dysfunction-associated steatohepatitis diagnosis and stratification
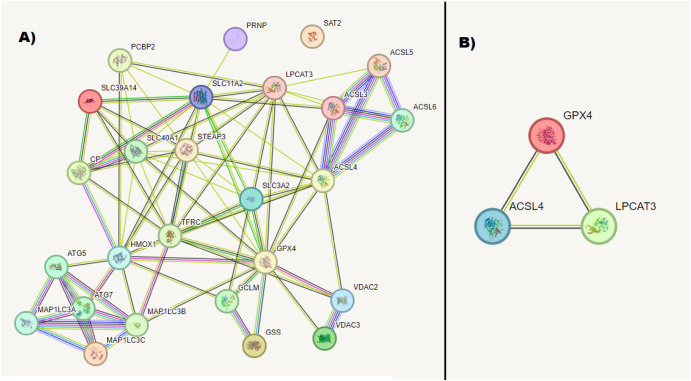
The global rise in Metabolic dysfunction-associated steatotic liver disease (MASLD)/Metabolic dysfunction-associated steatohepatitis (MASH) highlights the urgent necessity for noninvasive biomarkers to detect these conditions early. To address this, we endeavored to construct a diagnostic model for MASLD/MASH using a combination of bioinformatics, molecular/biochemical data, and machine learning techniques. Initially, bioinformatics analysis was employed to identify RNA molecules associated with MASLD/MASH pathogenesis and enriched in ferroptosis and exophagy. This analysis unveiled specific
Sentiment Analysis On Arabic Companies Reviews
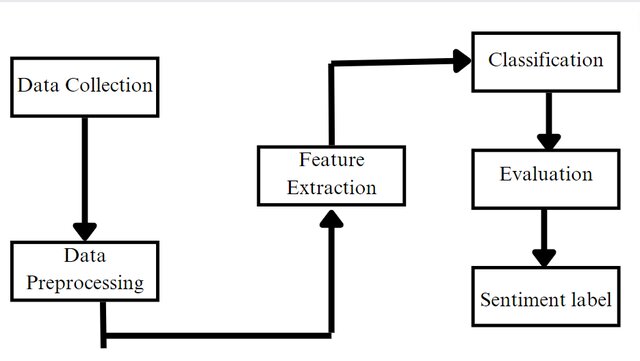
This study introduces an innovative approach to sentiment analysis, specifically tailored for the Arabic language, a domain that poses unique challenges due to its complex morphology and diverse dialects. Utilizing a substantial dataset of over 108,000 reviews related to Arabic companies, our primary objective was to develop a robust and reliable sentiment scoring system that caters to the intricacies of the Arabic language, aimed at assisting businesses in understanding customer sentiments more effectively.Our methodology encompassed an extensive preprocessing phase, crucial for preparing the
Machine Learning-Based Prediction of Backhaul Capacity Requirements for Cellular Networks
The accurate prediction of the required backhaul transmission capacity for cellular networks is critical to ensure efficient and reliable network performance, especially with the increasing demand for high-speed data services and the introduction of new radio technologies. This paper presents a framework for predicting the required capacity of backhaul networks based on the base stations' radio resources utilization and serving radio conditions. The proposed framework utilizes machine learning techniques to accurately estimate the required backhaul capacity by analyzing the base stations'
NileTMRG at SemEval-2017 Task 4: Arabic Sentiment Analysis
This paper describes two systems that were used by the NileTMRG for addressing Arabic Sentiment Analysis as part of SemEval-2017, task 4. NileTMRG participated in three Arabic related subtasks which are: Subtask A (Message Polarity Classification), Subtask B (Topic-Based Message Polarity classification) and Subtask D (Tweet quantification). For sub-task A, we made use of our previously developed sentiment analyzer which we augmented with a scored lexicon. For subtasks B and D, we used an ensemble of three different classifiers. The first classifier was a convolutional neural network for which
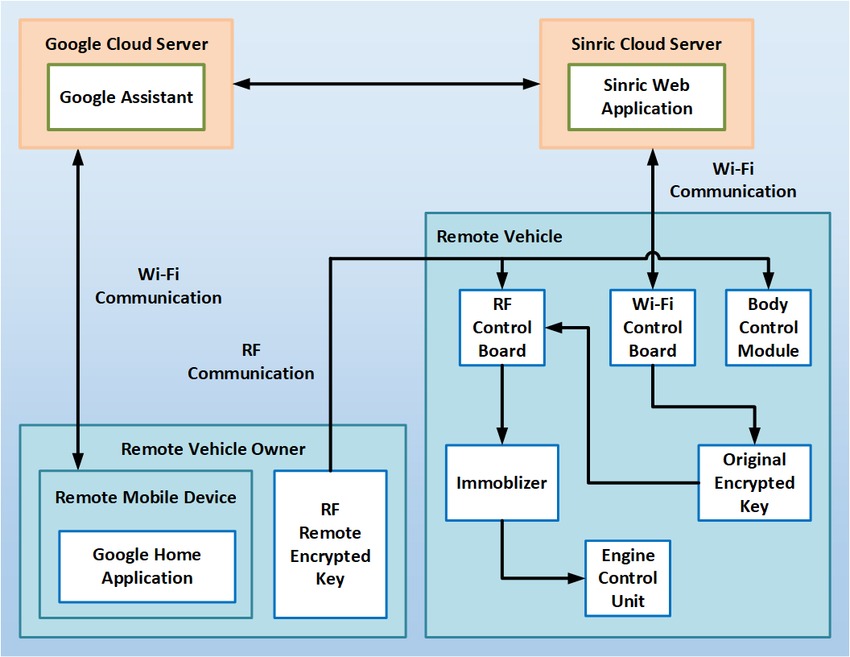
A Reliable Secure Architecture for Remote Wireless Controlling of Vehicle's Internal Systems based on Internet of Vehicles using RF and Wi-Fi
Internet of Vehicles is considered one of the most unprecedented outputs of the Internet of Things. No one has realized or even expected the rapidly-growing revolution regarding autonomous connected vehicles. Nowadays, Internet of Vehicles is massively progressing from Vehicular Ad-Hoc Networks as a huge futuristic research and development discipline. This paper proposes a novel reliable and secure architecture for ubiquitously controlling remote connected cars' internal systems, such as engine, doors' locks, sunroof, horn, windows' and lights' control systems. The main contribution is that
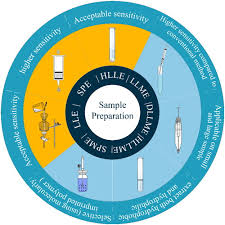
Analytical Methods for the Determination of Quercetin and Quercetin Glycosides in Pharmaceuticals and Biological Samples
Flavonoids are plant-derived compounds that have several health benefits, including antioxidative, anti-inflammatory, anti-mutagenic, and anti-carcinogenic effects. Quercetin is a flavonoid that is widely present in various fruits, vegetables, and drinks. Accurate determination of quercetin in different samples is of great importance for its potential health benefits. This review, is an overview of sample preparation and determination methods for quercetin in diverse matrices. Previous research on sample preparation and determination methods for quercetin are summarized, highlighting the

Sample preparation methods for determination of quercetin and quercetin glycosides in diverse matrices
Quercetin and its glycosides have gained a lot of interest due to their potential applications in preventing and treating various diseases. Quercetin is naturally available in free and glycoside forms such as isoquercitrin, rutin, avicularin, hyperoside, quercitrin, and others. These glycosides are more soluble and hence more bioavailable than quercetin. Determining the amount of quercetin in plants and foods is crucial to assess the quality of its natural sources, because the quercetin content changes with the species, variety, and the cultivation season. Furthermore, the concentrations of
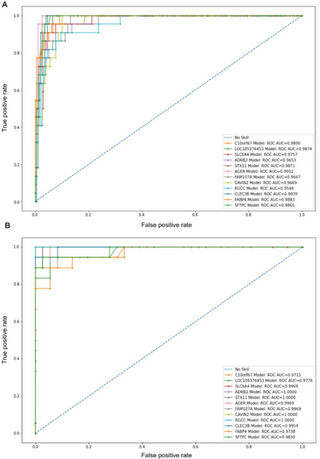
Comprehensive machine learning models for predicting therapeutic targets in type 2 diabetes utilizing molecular and biochemical features in rats
Introduction: With the increasing prevalence of type 2 diabetes mellitus (T2DM), there is an urgent need to discover effective therapeutic targets for this complex condition. Coding and non-coding RNAs, with traditional biochemical parameters, have shown promise as viable targets for therapy. Machine learning (ML) techniques have emerged as powerful tools for predicting drug responses. Method: In this study, we developed an ML-based model to identify the most influential features for drug response in the treatment of type 2 diabetes using three medicinal plant-based drugs (Rosavin, Caffeic
A feature selection-based framework to identify biomarkers for cancer diagnosis: A focus on lung adenocarcinoma
Lung cancer (LC) represents most of the cancer incidences in the world. There are many types of LC, but Lung Adenocarcinoma (LUAD) is the most common type. Although RNA-seq and microarray data provide a vast amount of gene expression data, most of the genes are insignificant to clinical diagnosis. Feature selection (FS) techniques overcome the high dimensionality and sparsity issues of the large-scale data. We propose a framework that applies an ensemble of feature selection techniques to identify genes highly correlated to LUAD. Utilizing LUAD RNA-seq data from the Cancer Genome Atlas (TCGA)

Vehicle to Pedestrian Systems: Survey, Challenges and Recent Trends
The accelerated rise of new technologies has reshaped the manufacturing industry of contemporary vehicles. Numerous technologies and applications have completely revolutionized the driving experience in terms of both safety and convenience. Although vehicles are now connected and equipped with a multitude of sensors and radars for collision avoidance, millions of people suffer serious accidents on the road, and unfortunately, the death rate is still on the rise. Collisions are still a dire reality for vehicles and pedestrians alike, which is why the improvement of collision prevention
Pagination
- Previous page ‹‹
- Page 19
- Next page ››
