Breadcrumb
Genomic landscape of hepatocellular carcinoma in Egyptian patients by whole exome sequencing
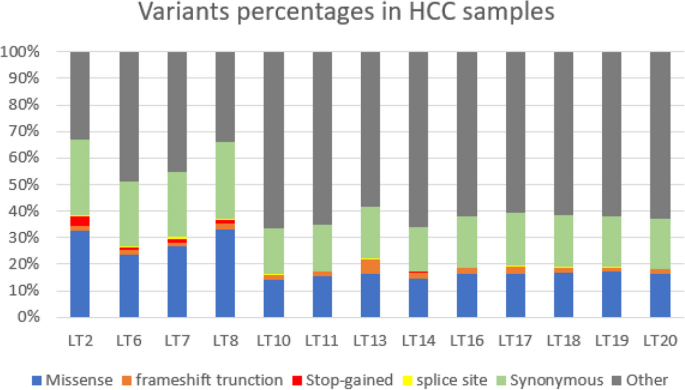
Background: Hepatocellular carcinoma (HCC) is the most common primary liver cancer. Chronic hepatitis and liver cirrhosis lead to accumulation of genetic alterations driving HCC pathogenesis. This study is designed to explore genomic landscape of HCC in Egyptian patients by whole exome sequencing. Methods: Whole exome sequencing using Ion Torrent was done on 13 HCC patients, who underwent surgical intervention (7 patients underwent living donor liver transplantation (LDLT) and 6 patients had surgical resection}. Results: Mutational signature was mostly S1, S5, S6, and S12 in HCC. Analysis of
Active Directory Attacks—Steps, Types, and Signatures
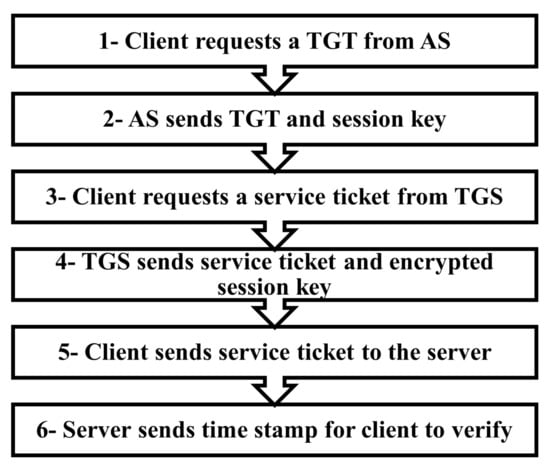
Active Directory Domain is a Microsoft service that allows and facilitates the centralized administration of all workstations and servers in any environment. Due to the wide use and adoption of this service, it has become a target for many attackers. Active Directory attacks have evolved through years. The attacks target different functions and features provided by Active Directory. In this paper, we provide insights on the criticality, impact, and detection of Active Directory attacks. We review the different Active Directory attacks. We introduce the steps of the Active Directory attack and
Hybrid Global Optimization Algorithm for Feature Selection
This paper proposes Parallelized Linear Time-Variant Acceleration Coefficients and Inertial Weight of Particle Swarm Optimization algorithm (PLTVACIW-PSO). Its designed has introduced the benefits of Parallel computing into the combined power of TVAC (Time-Variant Acceleration Coefficients) and IW (Inertial Weight). Proposed algorithm has been tested against linear, non-linear, traditional, and multiswarm based optimization algorithms. An experimental study is performed in two stages to assess the proposed PLTVACIW-PSO. Phase I uses 12 recognized Standard Benchmarks methods to evaluate the
MSDAR: Multi-Stage Dynamic Architecture Intrusion Detection System
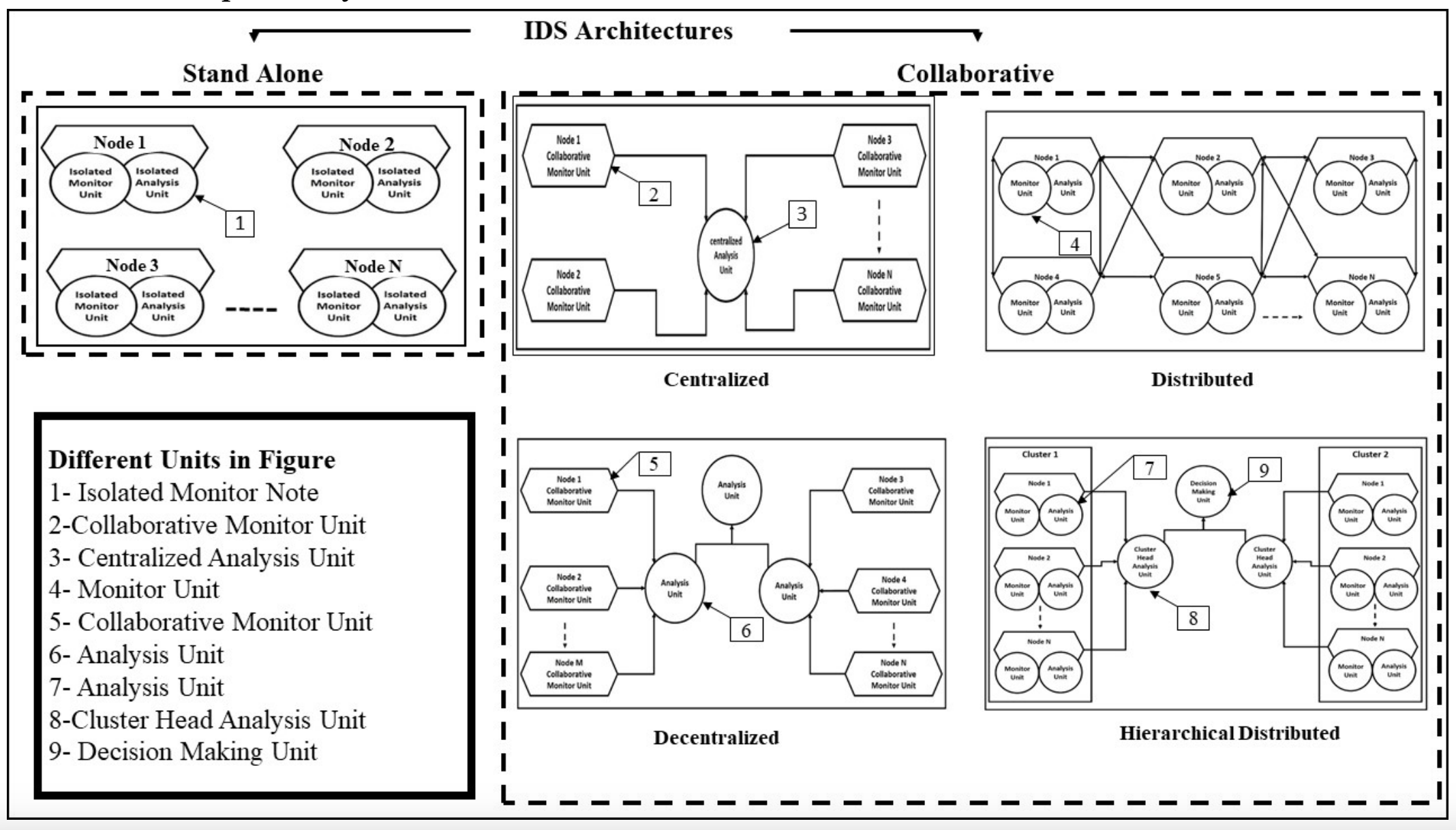
Ad hoc networks have been through extensive research in the last decade. Even with their desirable characteristics, major issues related to their security need to be considered. Various security solutions have been proposed to reduce the risks of malicious actions. They mainly focus on key management, authentication, secure localization, and aggregation techniques. These techniques have been proposed to secure wireless communications but they can only deal with external threats. Therefore, they are considered the first line of defense. Intrusion detection systems are always required to
New antileishmanial quinoline linked isatin derivatives targeting DHFR-TS and PTR1: Design, synthesis, and molecular modeling studies
In a search for new drug candidates for one of the neglected tropical diseases, leishmaniasis, twenty quinoline-isatin hybrids were synthesized and tested for their in vitro antileishmanial activity against Leishmania major strain. All the synthesized compounds showed promising in vitro activity against the promastigote form in a low micromolar range (IC50 = 0.5084–5.9486 μM) superior to the reference miltefosine (IC50 = 7.8976 μM). All the target compounds were then tested against the intracellular amastigote form and showed promising inhibition effects (IC50 = 0.60442–8.2948 μM versus 8.08

Uni-Buddy: A Multifunctional AI-Powered Assistant for Enhancing University Life: A Use Case at Nile University
Uni-Buddy is an advanced AI system developed to simplify university life at Nile University. It efficiently handles questions in everyday language, accesses real-time university databases, and simultaneously provides accurate responses for multiple users. Its goals include assisting with course registration, academic advising, financial inquiries, campus navigation, and research support. The evaluation demonstrates Uni-Buddy's user-friendly design, effective navigation, language comprehension, and database connectivity proficiency. Compared to similar studies, it stands out for its ease of use
Downlink Throughput Prediction in LTE Cellular Networks Using Time Series Forecasting
Long-Term Evolution (LTE) cellular networks have transformed the mobile business, as users increasingly require various network services such as video streaming, online gaming, and video conferencing. A network planning approach is required for network services to meet user expectations and meet their needs. The User DownLink (UE DL) throughput is considered the most effective Key Performance Indicator (KPI) for measuring the user experience. As a result, the forecast of UE DL throughput is essential in network dimensioning for the network planning team throughout the network design stage. The
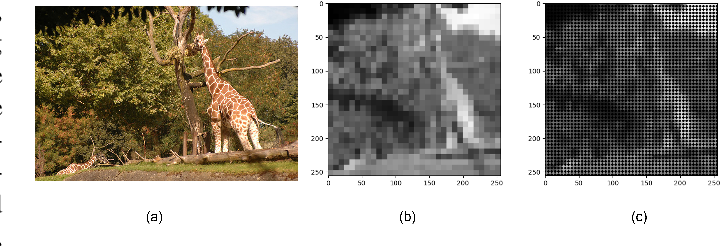
Enhancing Scene Simplification and Optimization for Retinal Prosthesis Platform
Retinal prostheses are designed to aid individuals with retinal degenerative conditions such as Retinitis Pigmentosa (RP) and Age-related Macular Degeneration (AMD). These prostheses seek to restore vision and improve the perceived scene by stimulating degenerated retinal cells using retinal stimulating electrodes. While these electrodes allow more efficient interaction with the surroundings, they offer limited resolution.This paper presents an innovative approach to revolutionize the visual perception of retinal prosthesis users. The key idea behind the proposed approach is to fuse

Sentiment-Based Spatiotemporal Prediction Framework for Pandemic Outbreaks Awareness Using Social Networks Data Classification
According to the World Health Organization, several factors have affected the accurate reporting of SARS-CoV-2 outbreak status, such as limited data collection resources, cultural and educational diversity, and inconsistent outbreak reporting from different sectors. Driven by this challenging situation, this study investigates the potential expediency of using social network data to develop reliable early information surveillance and warning system for pandemic outbreaks. As such, an enhanced framework of three inherently interlinked subsystems is proposed. The first subsystem includes data
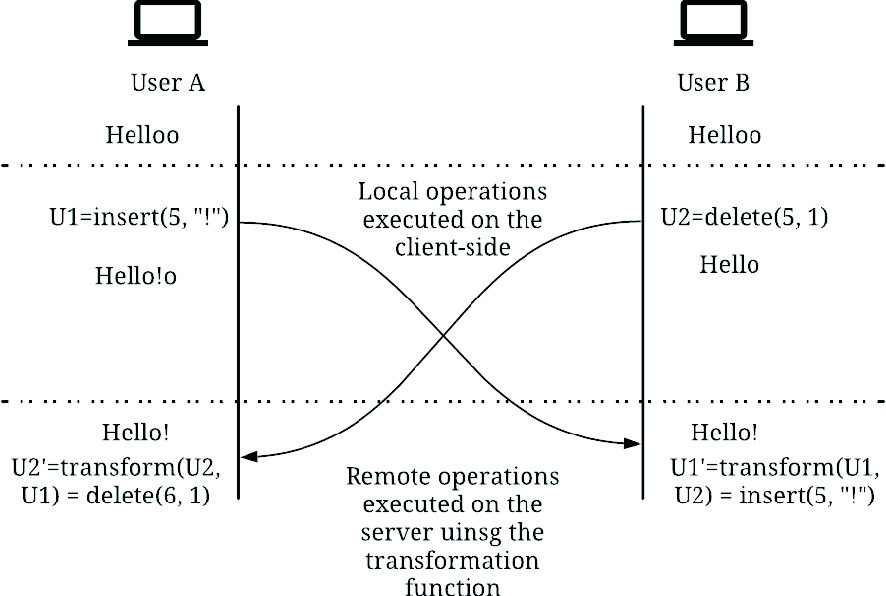
A Survey of Concurrency Control Algorithms in Collaborative Applications
Collaborative applications are becoming more prevalent for a variety of reasons, most important of which is the increased interest in remote work. In addition to adapting the business processes to a remote setting, designers of collaborative software have to decide on how their software can be used collaboratively. This paper discusses the two main technologies used to enable network-based real- or near-real-time collaborative software, namely Operational Transformation and Conflict-free Replicated Data Types. Recent developments in each technology are discussed, as well as a brief overview of
Pagination
- Page 1
- Next page ››
