Breadcrumb
A Comparative Analysis of Time Series Transformers and Alternative Deep Learning Models for SSVEP Classification
Steady State Visually Evoked Potentials (SSVEPs) are intrinsic responses to specific visual stimulus frequencies. When the retina is activated by a frequency ranging from 3.5 to 75 Hz, the brain produces electrical activity at the same frequency as the visual signal, or its multiples. Identifying the preferred frequencies of neurocortical dynamic processes is a benefit of SSVEPs. However, the time consumed during calibration sessions limits the number of training trials and gives rise to visual fatigue since there is significant human variation across and within individuals over time, which
Keyed Watermarks: A Fine-grained Tracking of Event-time in Apache Flink
Big Data Stream processing engines such as Apache Flink use windowing techniques to handle unbounded streams of events. Gathering all pertinent input within a window is crucial for event-time windowing since it affects how accurate results are. A significant part of this process is played by watermarks, which are unique timestamps that show the passage of events in time. However, the current watermark generation method in Apache Flink, which works at the level of the input stream, tends to favor faster sub-streams, resulting in dropped events from slower sub-streams. In our analysis, we found

Semi-Fragile Watermark for the Authentication and Recovery of Tampered Images
In order to strengthen the safety of corporate multimedia assets, a semi-fragile watermarking method is developed, which makes use of the integer wavelet transform (IWT) and the discrete cosine transform (DCT) for tamper detection and recovery. In this paper, we produce two distinct kinds of watermarks: an authentication watermark and a recovery watermark. A tamper detection methodology is utilized at the receiving end to check the watermarked image for validity and detect any assaults. If the changes are determined to be malicious, the suggested tamper recovery method is used to restore the

Bilingual Embeddings andWord Alignments for Translation Quality Estimation
This paper describes our submission UFAL MULTIVEC to the WMT16 Quality Estimation Shared Task, for English- German sentence-level post-editing effort prediction and ranking. Our approach exploits the power of bilingual distributed representations, word alignments and also manual post-edits to boost the performance of the baseline QuEst++ set of features. Our model outperforms the baseline, as well as the winning system in WMT15, Referential Translation Machines (RTM), in both scoring and ranking sub-tasks. © 2016 Association for Computational Linguistics.
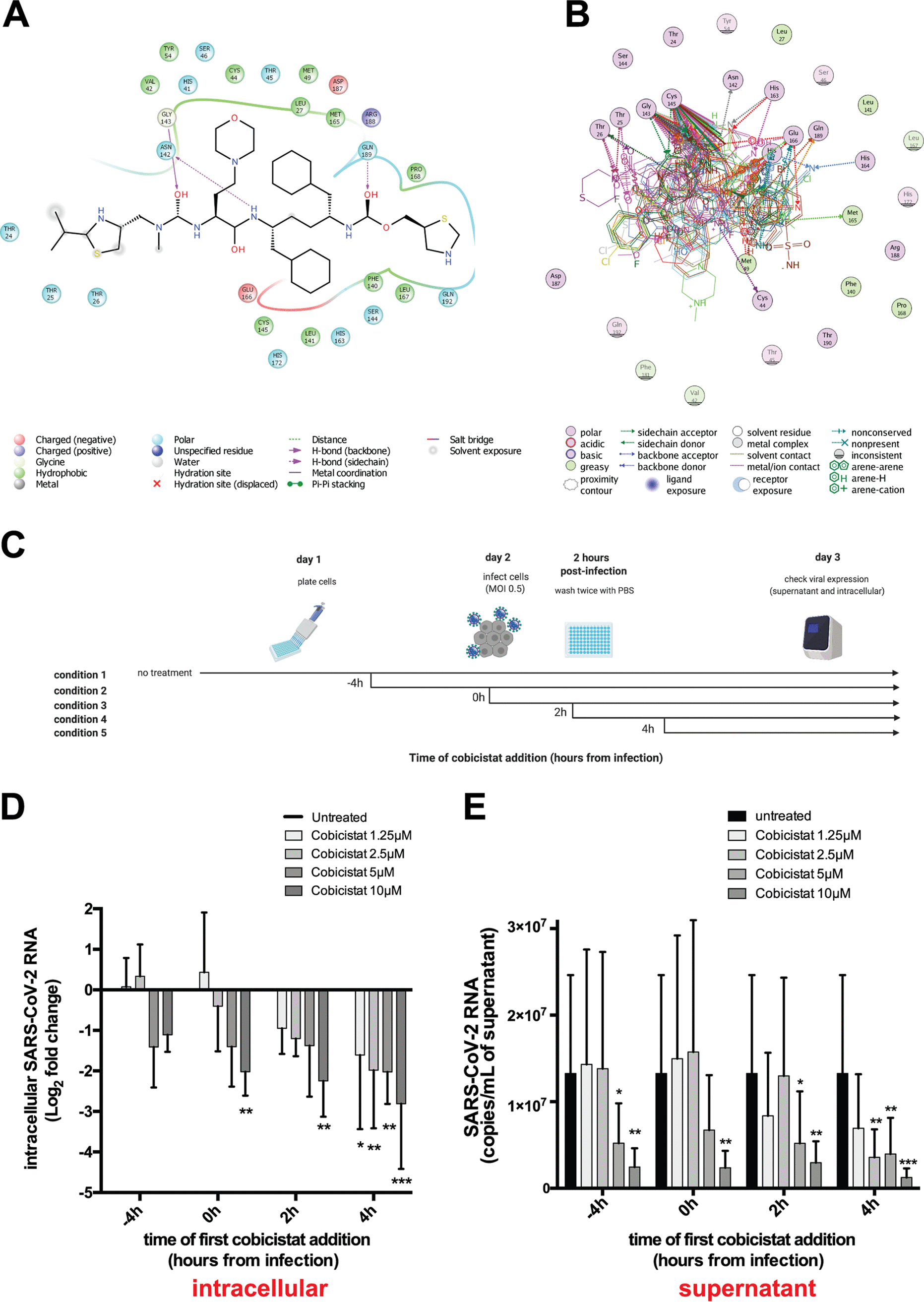
The FDA-Approved Drug Cobicistat Synergizes with Remdesivir to Inhibit SARS-CoV-2 Replication in Vitro and Decreases Viral Titers and Disease Progression in Syrian Hamsters
Combinations of direct-acting antivirals are needed to minimize drug resistance mutations and stably suppress replication of RNA viruses. Currently, there are limited therapeutic options against the severe acute respiratory syndrome coronavirus 2 (SARS-CoV-2), and testing of a number of drug regimens has led to conflicting results. Here, we show that cobicistat, which is an FDA-approved drug booster that blocks the activity of the drug-metabolizing proteins cytochrome P450-3As (CYP3As) and P-glycoprotein (P-gp), inhibits SARS-CoV-2 replication. Two independent cell-to-cell membrane fusion
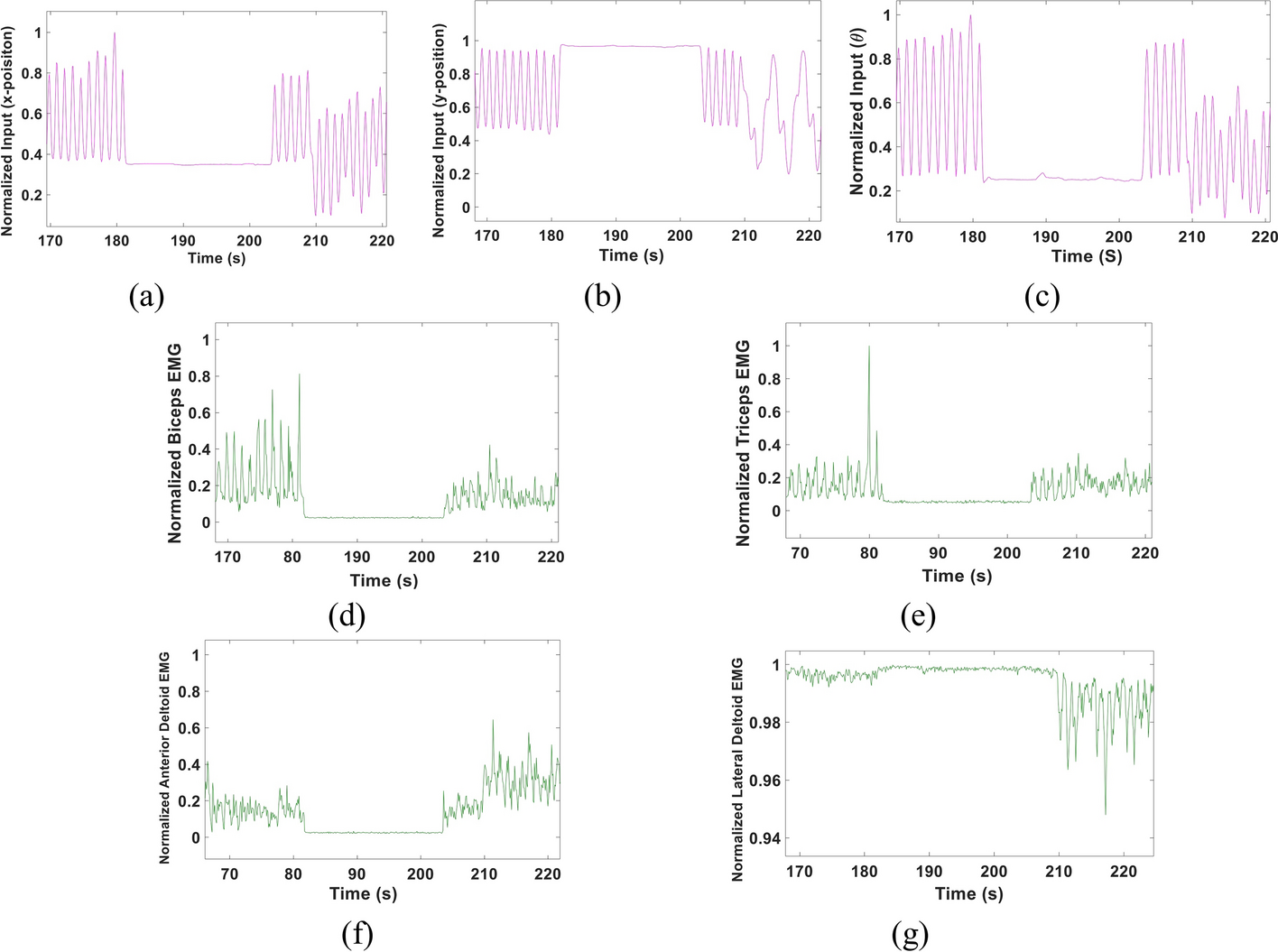
A multi-Kalman filter-based approach for decoding arm kinematics from EMG recordings
Background: Remarkable work has been recently introduced to enhance the usage of Electromyography (EMG) signals in operating prosthetic arms. Despite the rapid advancements in this field, providing a reliable, naturalistic myoelectric prosthesis remains a significant challenge. Other challenges include the limited number of allowed movements, lack of simultaneous, continuous control and the high computational power that could be needed for accurate decoding. In this study, we propose an EMG-based multi-Kalman filter approach to decode arm kinematics; specifically, the elbow angle (θ), wrist
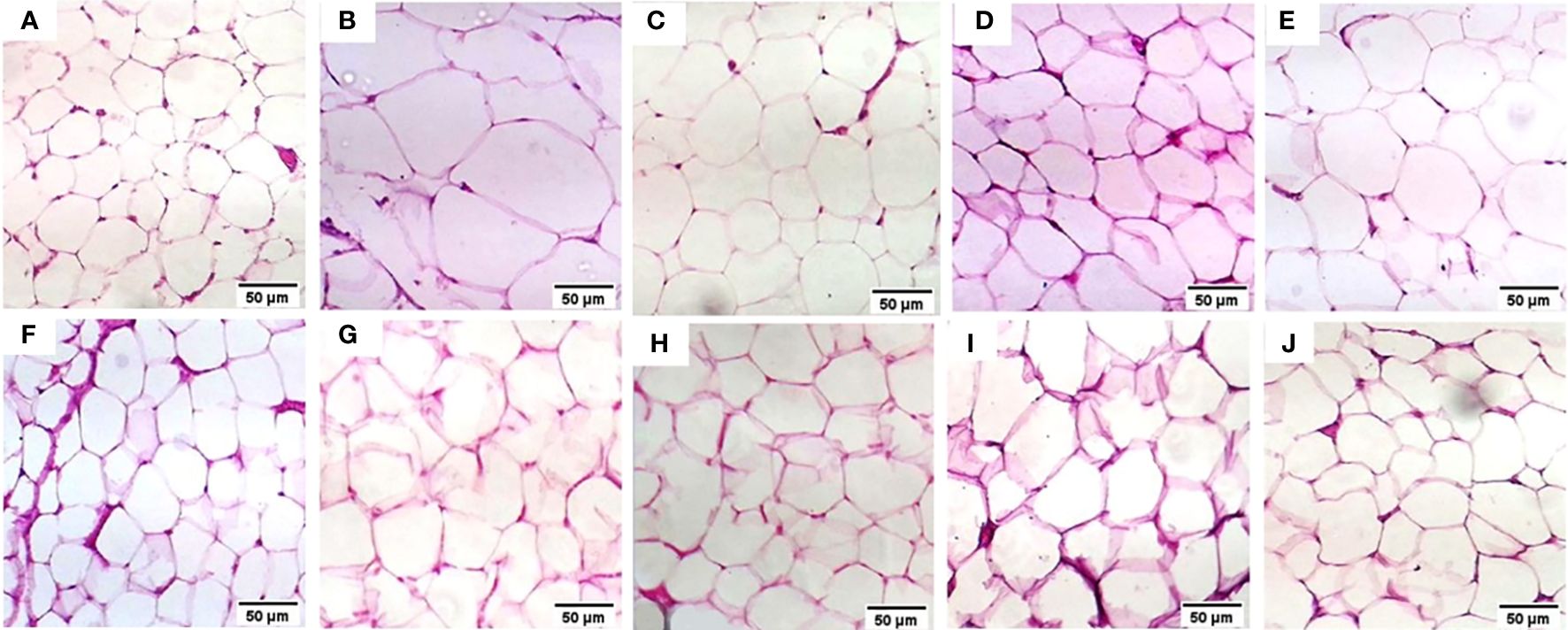
Comprehensive machine learning models for predicting therapeutic targets in type 2 diabetes utilizing molecular and biochemical features in rats
Introduction: With the increasing prevalence of type 2 diabetes mellitus (T2DM), there is an urgent need to discover effective therapeutic targets for this complex condition. Coding and non-coding RNAs, with traditional biochemical parameters, have shown promise as viable targets for therapy. Machine learning (ML) techniques have emerged as powerful tools for predicting drug responses. Method: In this study, we developed an ML-based model to identify the most influential features for drug response in the treatment of type 2 diabetes using three medicinal plant-based drugs (Rosavin, Caffeic
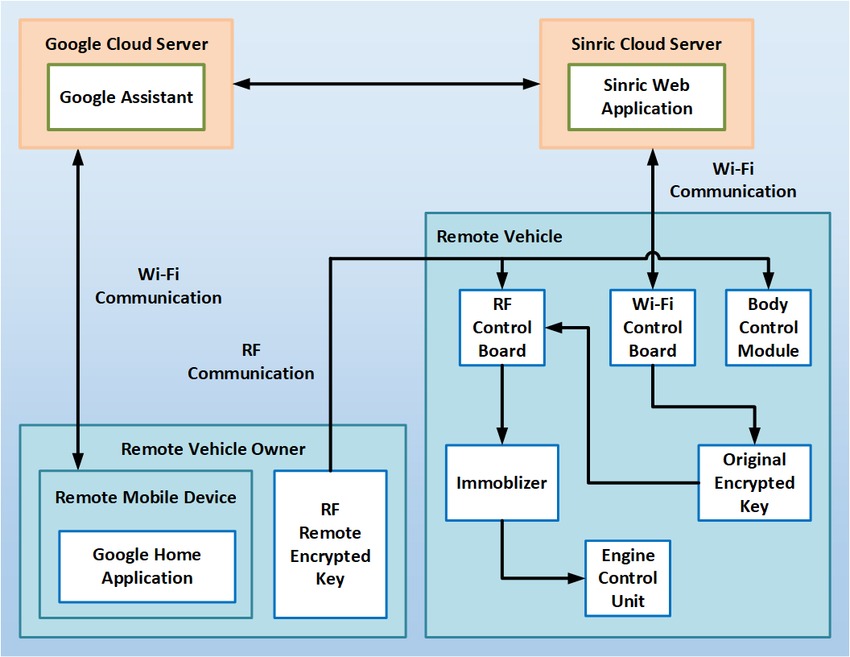
A Reliable Secure Architecture for Remote Wireless Controlling of Vehicle's Internal Systems based on Internet of Vehicles using RF and Wi-Fi
Internet of Vehicles is considered one of the most unprecedented outputs of the Internet of Things. No one has realized or even expected the rapidly-growing revolution regarding autonomous connected vehicles. Nowadays, Internet of Vehicles is massively progressing from Vehicular Ad-Hoc Networks as a huge futuristic research and development discipline. This paper proposes a novel reliable and secure architecture for ubiquitously controlling remote connected cars' internal systems, such as engine, doors' locks, sunroof, horn, windows' and lights' control systems. The main contribution is that
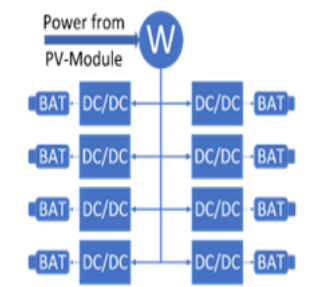
Developing Role Model of PV Powered Battery Swapping Stations for e-scooters in Urban Regions
Electric vehicles (EVs) can only provide lower carbon emissions than conventional, internal combustion-powered vehicles if they are charged using green energy. They also have the drawback of long charging times to 'refuel' them. To combat these two problems, a solar-powered battery charging and swapping station was developed using centered-human design and systems engineering. The design focuses on electric two-wheeled vehicles (e-scooters) due to the easier handling of their light and low-capacity batteries compared to electric cars. These stations are easy to maintain and manage and can be
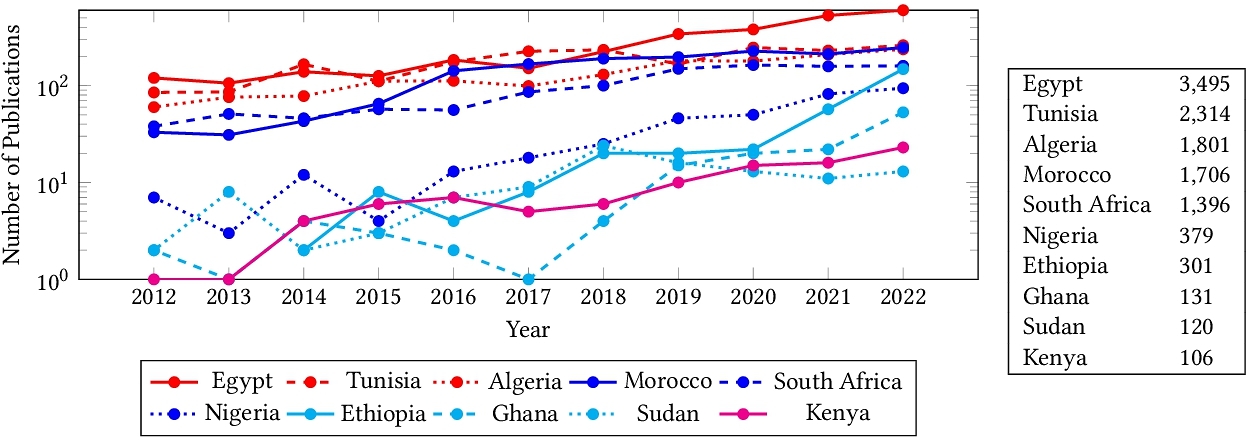
The State of Computer Vision Research in Africa
Despite significant efforts to democratize artificial intelligence (AI), computer vision which is a sub-field of AI, still lags in Africa. A significant factor to this, is the limited access to computing resources, datasets, and collaborations. As a result, Africa's contribution to top-tier publications in this field has only been 0.06% over the past decade. Towards improving the computer vision field and making it more accessible and inclusive, this study analyzes 63,000 Scopus-indexed computer vision publications from Africa. We utilize large language models to automatically parse their
Pagination
- Page 1
- Next page ››
